Solving the BrainPan Vulnhub
This article is going to walk through the step I used to solve the Brainpan vulnerable VMs that can be download at the https://www.vulnhub.com/entry/brainpan-1,51/
The objective of the game
Using a buffer overflow attack to break the system and get the root access
Tools used on this game
- Kali 64bits (192.168.187.135)
- netdiscover
- NMAP
- Nikto
- metasploit-framework
- immunity debugger
Game Setup
1) Downloaded the Brainpan system at VulnHub to start the game using any VM client. The VMware Workstation 15 was used for this walkthrough.
Information Gathering
2) Used netdiscover to find the target machine IP address
2) Used netdiscover to find the target machine IP address
3) Gathered some information about the target machine
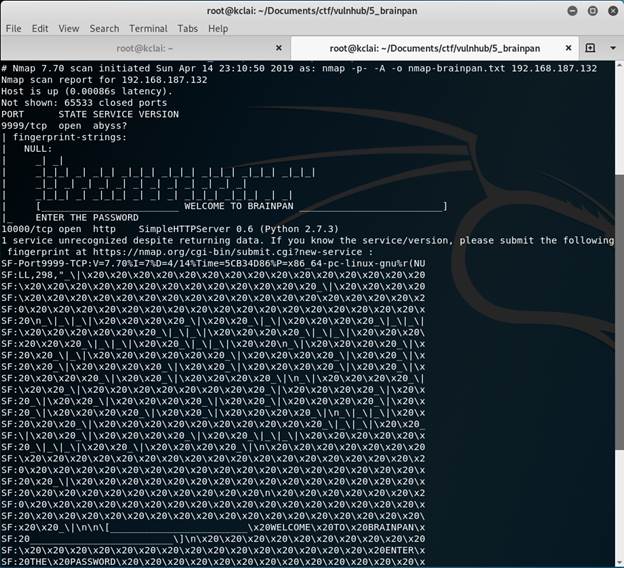
nmap -p- -A -oN nmap-brainpan.txt 192.168.187.132
Two ports opened which were 9999 for unknown service and 10000 for HTTP web
4) Visit the website http://192.168.187.132:10000/
6) A /bin/ directory was found and get a file brainpan.exe
7) Downloaded and checked the file
7) Downloaded and checked the file
7) Downloaded and checked the file








No comments:
Post a Comment